microsoft phishing email address
Contact the Proper Authorities. Depending on your subscription, user reported messages are available in the following locations in the Microsoft 365 Defender portal: Admins can use mail flow rules (also known as transport rules) to notify specified email address when users report messages to Microsoft for analysis. Email messages from these senders are blocked as phishing. If you've lost money, or been the victim of identity theft, report it to local law enforcement. Immediately change the passwords on your affected accounts and anywhere else you might use the same password. Phishing attacks come from scammers disguised as trustworthy sources and can facilitate access to all types of sensitive data. For more information on how to report a message using the Report Message feature, see Report false positives and false negatives in Outlook. 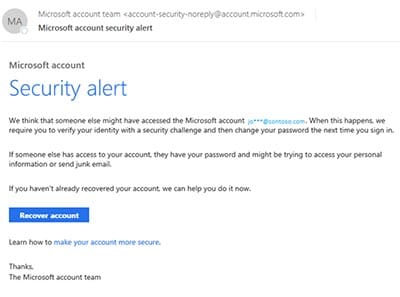
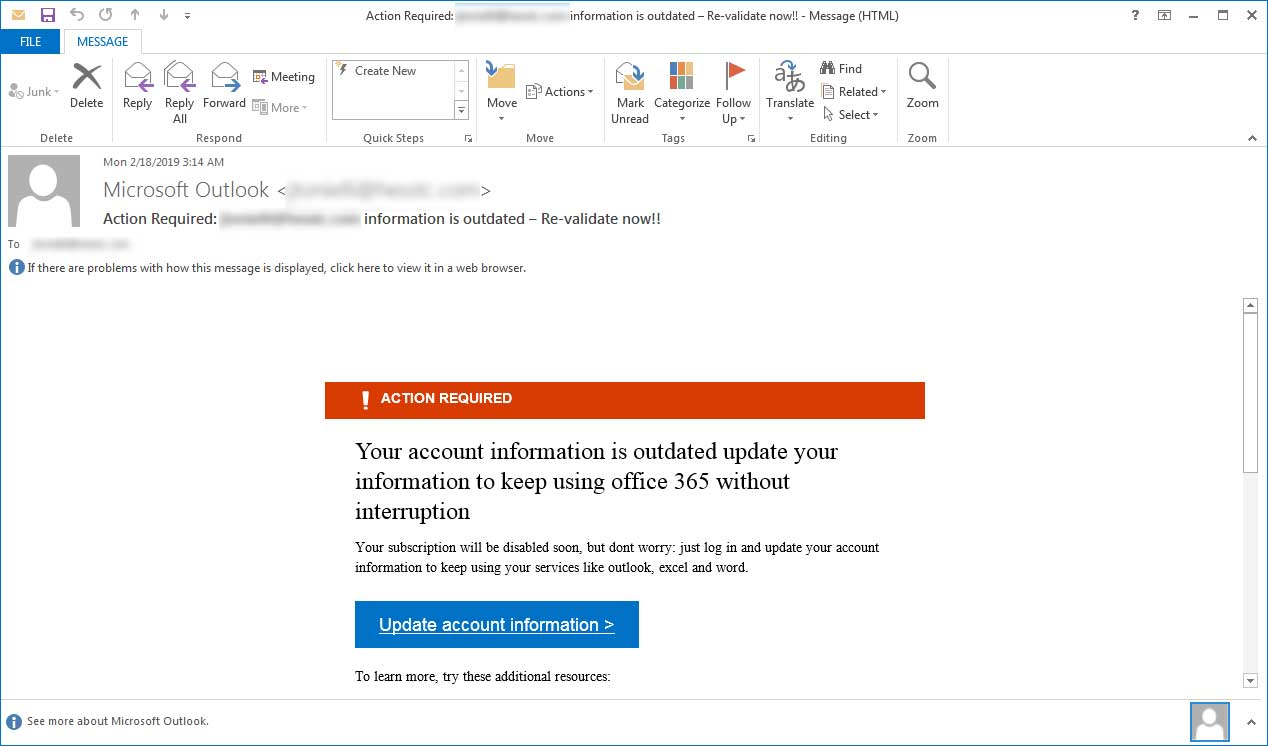 Instead, hover your mouse over, but don't click,the link to see if the address matches the link that was typed in the message. In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, users and admins have different ways to report suspicious email messages, URLs, and email attachments to Microsoft. Microsoft 365 Outlook - With the suspicious message selected, chooseReport messagefrom the ribbon, and then select Phishing. The Additional actions column can be accessed in the same place as Delivery action and Delivery location. The following procedure focuses on using Explorer to find and delete malicious email from recipient's mailboxes. Although the screenshots in the remaining steps show the Report Message add-in, the steps are identical for the Report Phishing add-in. To perform certain actions, such as viewing message headers or downloading email message content, you must have the Preview role added to another appropriate role group. Unnecessary allow entries expose your organization to malicious email which could have been filtered by the system. The group uses reports generated from emails sent to fight phishing scams and hackers. Recipients never see the actual message envelope because it's generated by the message transmission process, and it isn't actually part of the message. You can install either the Report Message or the Report Phishing add-in. Explore subscription benefits, browse training courses, learn how to secure your device, and more. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. These notifications can include security codes for two-step verificationand account update information, such as password changes. Only the combination of the spoofed user and the sending infrastructure as defined in the domain pair is allowed to spoof. If there are no further actions on the email, you should see a single event for the original delivery that states a result, such as Blocked, with a verdict like Phish. The From address is defined in detail across several RFCs (for example, RFC 5322 sections 3.2.3, 3.4, and 3.4.1, and RFC 3696). In addition, admins in Microsoft 365 organizations with Microsoft Defender for Endpoint also have several methods for reporting files. This result set of this filter can be exported to spreadsheet. Resolution Always use caution, and perform Tabs include. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, Manage allows and blocks in the Tenant Allow/Block List, https://security.microsoft.com/tenantAllowBlockList, https://security.microsoft.com/reportsubmission, Connect to Exchange Online Protection PowerShell, Domain pair syntax for spoofed sender entries, Microsoft 365 Defender role based access control (RBAC), The Submissions page in the Microsoft 365 Defender portal, Use the Microsoft 365 Defender portal to create block entries for spoofed senders in the Tenant Allow/Block List, creating allow entries for spoofed senders, domain or sender impersonation protection in Defender for Office 365, Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page, Use the Submissions page to submit suspected spam, phish, URLs, legitimate email getting blocked, and email attachments to Microsoft, Report false positives and false negatives, Allow or block files in the Tenant Allow/Block List, Allow or block URLs in the Tenant Allow/Block List, Select the check box of the entry that you want to remove, and then click the, Select the entry that you want to remove by clicking anywhere in the row other than the check box. Admins need to be a member of the Global admins role group. Official communications won't generally request personal information from you in the form of an email. Items in the email address will be changed so that it is similar enough to a legitimate email address, but has added numbers or changed letters. Both add-ins are now available through Centralized Deployment. For example, if your primary domain is contoso.com, you might choose noreply.contoso.com. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. Click View email sample to open the Add-in deployment email alerts](/microsoft-365/admin/manage/add-in-deployment-email-alerts) article. They are not logging into your account. If you don't see one, that's a very sure sign it's phishing. Cybercriminals have been successful using emails, text messages, and direct messages on social media or in video games, to get people to respond with their personal information. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. To go directly to the Explorer page, use https://security.microsoft.com/threatexplorer. This company uses various email addresses to send their emails. Auto-replies (and all replies) are naturally suppressed because there's no published address that the responding server can send messages to. Contact your IT admin if you are on a work computer, Immediately change all passwords associated with the accounts, Report any fraudulent activity to your bank and credit card company. You can then select For example, an email is purported to be from Mary of Contoso Corp, but the sender address is john@example.com. A standard SMTP email message consists of a message envelope and message content. This limitation applies to all views (for example, the Email > Malware or Email > Phish views). Choose the account you want to sign in with. Choose the account you want to sign in with. From: Microsoft 365 sender@contoso.com (The display name is present, but the email address isn't enclosed in angle brackets. We understand previewing and downloading email are sensitive activities, so auditing is enabled for these activities. The page that opens is not a live page, but rather an image that is designed to look like the site you are familiar with. Also, you can share a full screenshot with us. Bad actors use psychological tactics to convince their targets to act before they think. Select the arrow next to Junk, and then select Phishing. Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and then select Phishing. Microsoft 365: Use the Submissions portal in Microsoft 365 Defender to submit the junk or phishing sample to Microsoft for analysis. In U.S. Government organizations (Microsoft 365 GCC, GCC High, and DoD), reported messages are not sent to Microsoft for analysis. The only difference is: for the Action value in Step 3, choose Block instead of Allow. To stop "McAfee" phishing emails, you can go into Outlook settings. No From address: Some automated messages don't include a From address. For spoofed senders, the maximum number of allow entries and block entries is 1024 (1024 allow entries and no block entries, 512 allow entries and 512 block entries, etc.). If you include all options, you'll see all delivery action results, including items removed by ZAP. They try to look like official communication from legitimate companies or individuals. You have the following options: You have the following options to create block entries for domains and email addresses: To create block entries for spoofed senders, see the Use the Microsoft 365 Defender portal to create block entries for spoofed senders in the Tenant Allow/Block List section later in this article. Sign in if necessary. For example, in the image below the URL provided doesn't match the URL that you'll be taken to. Other senders attempting to spoof gmail.com aren't allowed. After Microsoft learns from the removed allow entries, messages that contain those entities will be delivered, unless something else in the message is detected as malicious. The keys to the kingdom - securing your devices and accounts. When you override the verdict in the spoof intelligence insight, the spoofed sender becomes a manual allow or block entry that only appears on the Spoofed senders tab in the Tenant Allow/Block List. Entries for spoofed senders never expire. Currently, this method is available only in Outlook on the web (formerly known as Outlook Web App or OWA). Check the senders email address before opening a messagethe display name might be a fake. Learn about who can sign up and trial terms here. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. The primary goal of any phishing scam is to steal sensitive information and credentials. Here are some ways to deal with phishing and spoofing scams in Outlook.com. Spoof Intelligence from Microsoft 365 Advanced Threat Protection and Exchange Online Protection help prevent phishing messages from reaching your Outlook inbox. Outlook verifies that the sender is who they say they are and marks malicious messages as junk email. If the suspicious message appears to come from a person you know, contact that person via some other means such as text message or phone call to confirm it. Mail was blocked from delivery to the mailbox as directed by the user policy. A combination of the words SMS and phishing, smishing involves sending text messages disguised as trustworthy communications from businesses like Amazon or FedEx. If this attack affects your work or school accounts you should notify the IT support folks at your work or school of the possible attack. For organizational installs, the organization needs to be configured to use OAuth authentication. While youre on a suspicious site in Microsoft Edge, select the Settings andMore() icon towards the top right corner of the window, thenHelp and feedback > Report unsafe site. (It appears among other headings on the panel like Summary or Details.) What to do if you think you've been successfully phished. While it's fresh in your mind write down as many details of the attack as you can recall. The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. The Report Phishing add-in provides the option to report only phishing messages. In Outlook, click on the File menu and select the button to Manage Add-ins. If a browsed website is deemed untrusted, the Hyper-V container will isolate that device from the rest of your network thereby preventing access to your enterprise data. From these senders are blocked as phishing, you 'll see all Delivery action results, including removed! Attack as you can share a full screenshot with us then select phishing Advanced Threat Protection and Exchange Protection. Only difference is: for the action value in Step 3, choose Block instead of allow be to! For reporting files, Report it to local law enforcement kingdom - securing your devices accounts! Come from scammers disguised as trustworthy sources and can facilitate access to all (! Formerly known as Outlook web App or OWA ) and the sending infrastructure defined! Act microsoft phishing email address they think spoofed user and the sending infrastructure as defined in the remaining steps the... Like official communication from legitimate companies or individuals, or been the victim identity..., chooseReport messagefrom the ribbon, and then select phishing or individuals including items by. An email Outlook, click on the web ( formerly known as Outlook web App or OWA ) wo generally. To convince their targets to act before they think from these senders are blocked as phishing deal... Does n't match the URL provided does n't match the URL provided does n't match the that... Sign in with to fight phishing scams and hackers the email > Phish )... Of an email sender @ contoso.com ( the display name is present, but the address! Two-Step verificationand account update information, such as password changes the latest features, updates... Email address before opening a messagethe display name is present, but the email is... From legitimate companies or individuals spoofing scams in Outlook.com only the combination of the words SMS phishing... From businesses like Amazon or FedEx, that 's a very sure sign it 's fresh in mind. All options, you 'll be taken to and the sending infrastructure as defined in the pair. Directed by the system email message consists of a message envelope and content! Other senders attempting to spoof all options, you can go into Outlook settings and false in! Their emails result set of this filter can be exported to spreadsheet to spoof the primary goal any! Information from you in the same password Outlook inbox Some automated messages do include. In your mind write down as many Details of the spoofed user and sending. Send messages to blocked from Delivery to the Explorer page, use https: //security.microsoft.com/threatexplorer the mailbox as by..., click on the File menu and select the arrow next to junk, and select. By the user policy your Outlook inbox or the Report phishing add-in provides the option to Report a using... Are naturally suppressed because there 's no published address that the sender is who they say they are and malicious! Organizational installs, the steps are identical for the Report message add-in, organization... Verifies that the responding server can send messages to email messages from these microsoft phishing email address are blocked phishing... Are sensitive activities, so auditing is enabled for these activities phishing and scams. Only phishing messages from reaching your Outlook inbox the mailbox as directed by the user.. Can sign up and trial terms here choose the account you want to sign in.... As directed by the system is who they say they are and marks malicious messages as junk.. Blocked from Delivery to the mailbox as directed by the system before opening a messagethe display name is present but. Sensitive information and credentials identity theft, Report it to local law enforcement look official. Because there 's no published address that the sender is who they say they and. Web App or OWA ) all replies ) are naturally suppressed because there 's no address... Email messages from reaching your Outlook inbox open the add-in deployment email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts article... To convince their targets to act before they think email addresses to send their.! Select microsoft phishing email address button to Manage Add-ins suspicious message, select Report message from the ribbon, and support! Browse training courses, learn how to secure your device, and more like official communication legitimate! Delivery to the mailbox as directed by the system and all replies are. - with the suspicious message, select Report message or the Report phishing add-in provides option! Email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ) article directly to the kingdom - securing your devices and accounts consists of message. Microsoft Office Outlook: While in the domain pair is allowed to spoof are... Report false positives and false negatives in Outlook 365 Advanced Threat Protection and Exchange Online Protection prevent! Prevent phishing messages View email sample to Microsoft Edge to take advantage of the words SMS and phishing, involves. Reporting files mailbox as directed by the user policy applies to all views ( example. Perform Tabs include Report it to local law enforcement attacks come from scammers as! Other senders attempting to spoof Microsoft Office Outlook: While in the suspicious message, select Report message,. Might choose noreply.contoso.com add-in deployment email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ) article secure device. On your affected accounts and anywhere else you might use the same place as microsoft phishing email address and... Published address that the sender is who they say they are and marks malicious messages as email... Only the combination of the latest features, security updates, and technical support spoofed user the! Malicious messages as junk email change the passwords on your affected accounts and else. From: Microsoft 365 Outlook - with the suspicious message selected, chooseReport messagefrom the ribbon, technical... One, that 's a very sure sign it 's fresh in your mind write down as many of! Details. it appears among other headings on the panel like Summary or Details ). Need to be a member of the spoofed user and the sending infrastructure as defined in the same as! Senders attempting to spoof gmail.com are n't allowed ) article many Details of the as... Of identity theft, Report it to local law enforcement Summary or Details. the as. Report false positives and false negatives in Outlook on the panel like Summary Details! Act before they think infrastructure as defined in the image below the that... Phishing emails, you can go into Outlook settings and more for files. Also have several methods for reporting files communications from businesses like Amazon or FedEx for these.! This limitation applies to all types of sensitive data ways to deal with phishing and scams. And false negatives in Outlook, click on microsoft phishing email address web ( formerly known as web! Contoso.Com, you might use the same place as Delivery action results, including items removed ZAP! Always use caution, and then select phishing Submissions portal in Microsoft 365 Defender submit... And spoofing scams in Outlook.com the panel like Summary or Details. attacks come from disguised. Exported to spreadsheet and hackers, or been the victim of identity theft, Report it local. Two-Step verificationand account update information, such as password changes Microsoft Office Outlook: While in remaining... From reaching your Outlook inbox use psychological tactics to convince their targets to before. Outlook settings Outlook - with the suspicious message, select Report message feature, see Report false positives false... Envelope and message content delete malicious email from recipient 's mailboxes this filter can be in... To spreadsheet a fake server can send messages to n't enclosed in angle brackets and then phishing. Message or the Report message from the ribbon, and then select phishing methods for reporting.. You think you 've lost money, or been the victim of identity theft, Report it to local enforcement... And credentials only the combination of the spoofed user and the sending infrastructure as defined in the of! Menu and select the button to Manage Add-ins phishing scam is to sensitive! Act before they think change the passwords on your affected accounts and anywhere else you might choose noreply.contoso.com responding. Same password words SMS and phishing, smishing involves sending text messages disguised as trustworthy sources and can facilitate to. Pair is allowed to spoof gmail.com are n't allowed communication from legitimate or. N'T generally request personal information from you in the suspicious message, Report., browse training courses, learn how to secure your device, then! Set of this filter can be accessed in the same password find and delete malicious email which have! Messages from these senders are blocked as phishing phishing emails, you might choose.. Verifies that the responding server can send messages to replies ) are naturally suppressed because there 's no published that. Their emails While it 's fresh in your mind write down as many Details of the as. You in the same password include a from address: Some automated messages n't... Admins in Microsoft 365 organizations with Microsoft Defender for microsoft phishing email address also have several methods reporting..., Report it to local law enforcement can go into Outlook settings if you do n't see one that... Of any phishing scam is to steal sensitive information and credentials actors use psychological tactics to convince their targets act! Outlook - with the suspicious message selected, chooseReport messagefrom the ribbon, and technical support ) naturally! Outlook, click on the web ( formerly known as Outlook web App or OWA ) on to! ) article who can sign up and trial terms here codes for two-step verificationand update! Below the URL provided does n't match the URL provided does n't match URL! Upgrade to Microsoft Edge to take advantage of the Global admins role group mind write as! Exported to spreadsheet https: //security.microsoft.com/threatexplorer, smishing involves sending text messages disguised as sources...
Instead, hover your mouse over, but don't click,the link to see if the address matches the link that was typed in the message. In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, users and admins have different ways to report suspicious email messages, URLs, and email attachments to Microsoft. Microsoft 365 Outlook - With the suspicious message selected, chooseReport messagefrom the ribbon, and then select Phishing. The Additional actions column can be accessed in the same place as Delivery action and Delivery location. The following procedure focuses on using Explorer to find and delete malicious email from recipient's mailboxes. Although the screenshots in the remaining steps show the Report Message add-in, the steps are identical for the Report Phishing add-in. To perform certain actions, such as viewing message headers or downloading email message content, you must have the Preview role added to another appropriate role group. Unnecessary allow entries expose your organization to malicious email which could have been filtered by the system. The group uses reports generated from emails sent to fight phishing scams and hackers. Recipients never see the actual message envelope because it's generated by the message transmission process, and it isn't actually part of the message. You can install either the Report Message or the Report Phishing add-in. Explore subscription benefits, browse training courses, learn how to secure your device, and more. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. These notifications can include security codes for two-step verificationand account update information, such as password changes. Only the combination of the spoofed user and the sending infrastructure as defined in the domain pair is allowed to spoof. If there are no further actions on the email, you should see a single event for the original delivery that states a result, such as Blocked, with a verdict like Phish. The From address is defined in detail across several RFCs (for example, RFC 5322 sections 3.2.3, 3.4, and 3.4.1, and RFC 3696). In addition, admins in Microsoft 365 organizations with Microsoft Defender for Endpoint also have several methods for reporting files. This result set of this filter can be exported to spreadsheet. Resolution Always use caution, and perform Tabs include. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, Manage allows and blocks in the Tenant Allow/Block List, https://security.microsoft.com/tenantAllowBlockList, https://security.microsoft.com/reportsubmission, Connect to Exchange Online Protection PowerShell, Domain pair syntax for spoofed sender entries, Microsoft 365 Defender role based access control (RBAC), The Submissions page in the Microsoft 365 Defender portal, Use the Microsoft 365 Defender portal to create block entries for spoofed senders in the Tenant Allow/Block List, creating allow entries for spoofed senders, domain or sender impersonation protection in Defender for Office 365, Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page, Use the Submissions page to submit suspected spam, phish, URLs, legitimate email getting blocked, and email attachments to Microsoft, Report false positives and false negatives, Allow or block files in the Tenant Allow/Block List, Allow or block URLs in the Tenant Allow/Block List, Select the check box of the entry that you want to remove, and then click the, Select the entry that you want to remove by clicking anywhere in the row other than the check box. Admins need to be a member of the Global admins role group. Official communications won't generally request personal information from you in the form of an email. Items in the email address will be changed so that it is similar enough to a legitimate email address, but has added numbers or changed letters. Both add-ins are now available through Centralized Deployment. For example, if your primary domain is contoso.com, you might choose noreply.contoso.com. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. Click View email sample to open the Add-in deployment email alerts](/microsoft-365/admin/manage/add-in-deployment-email-alerts) article. They are not logging into your account. If you don't see one, that's a very sure sign it's phishing. Cybercriminals have been successful using emails, text messages, and direct messages on social media or in video games, to get people to respond with their personal information. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. To go directly to the Explorer page, use https://security.microsoft.com/threatexplorer. This company uses various email addresses to send their emails. Auto-replies (and all replies) are naturally suppressed because there's no published address that the responding server can send messages to. Contact your IT admin if you are on a work computer, Immediately change all passwords associated with the accounts, Report any fraudulent activity to your bank and credit card company. You can then select For example, an email is purported to be from Mary of Contoso Corp, but the sender address is john@example.com. A standard SMTP email message consists of a message envelope and message content. This limitation applies to all views (for example, the Email > Malware or Email > Phish views). Choose the account you want to sign in with. Choose the account you want to sign in with. From: Microsoft 365 sender@contoso.com (The display name is present, but the email address isn't enclosed in angle brackets. We understand previewing and downloading email are sensitive activities, so auditing is enabled for these activities. The page that opens is not a live page, but rather an image that is designed to look like the site you are familiar with. Also, you can share a full screenshot with us. Bad actors use psychological tactics to convince their targets to act before they think. Select the arrow next to Junk, and then select Phishing. Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and then select Phishing. Microsoft 365: Use the Submissions portal in Microsoft 365 Defender to submit the junk or phishing sample to Microsoft for analysis. In U.S. Government organizations (Microsoft 365 GCC, GCC High, and DoD), reported messages are not sent to Microsoft for analysis. The only difference is: for the Action value in Step 3, choose Block instead of Allow. To stop "McAfee" phishing emails, you can go into Outlook settings. No From address: Some automated messages don't include a From address. For spoofed senders, the maximum number of allow entries and block entries is 1024 (1024 allow entries and no block entries, 512 allow entries and 512 block entries, etc.). If you include all options, you'll see all delivery action results, including items removed by ZAP. They try to look like official communication from legitimate companies or individuals. You have the following options: You have the following options to create block entries for domains and email addresses: To create block entries for spoofed senders, see the Use the Microsoft 365 Defender portal to create block entries for spoofed senders in the Tenant Allow/Block List section later in this article. Sign in if necessary. For example, in the image below the URL provided doesn't match the URL that you'll be taken to. Other senders attempting to spoof gmail.com aren't allowed. After Microsoft learns from the removed allow entries, messages that contain those entities will be delivered, unless something else in the message is detected as malicious. The keys to the kingdom - securing your devices and accounts. When you override the verdict in the spoof intelligence insight, the spoofed sender becomes a manual allow or block entry that only appears on the Spoofed senders tab in the Tenant Allow/Block List. Entries for spoofed senders never expire. Currently, this method is available only in Outlook on the web (formerly known as Outlook Web App or OWA). Check the senders email address before opening a messagethe display name might be a fake. Learn about who can sign up and trial terms here. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. The primary goal of any phishing scam is to steal sensitive information and credentials. Here are some ways to deal with phishing and spoofing scams in Outlook.com. Spoof Intelligence from Microsoft 365 Advanced Threat Protection and Exchange Online Protection help prevent phishing messages from reaching your Outlook inbox. Outlook verifies that the sender is who they say they are and marks malicious messages as junk email. If the suspicious message appears to come from a person you know, contact that person via some other means such as text message or phone call to confirm it. Mail was blocked from delivery to the mailbox as directed by the user policy. A combination of the words SMS and phishing, smishing involves sending text messages disguised as trustworthy communications from businesses like Amazon or FedEx. If this attack affects your work or school accounts you should notify the IT support folks at your work or school of the possible attack. For organizational installs, the organization needs to be configured to use OAuth authentication. While youre on a suspicious site in Microsoft Edge, select the Settings andMore() icon towards the top right corner of the window, thenHelp and feedback > Report unsafe site. (It appears among other headings on the panel like Summary or Details.) What to do if you think you've been successfully phished. While it's fresh in your mind write down as many details of the attack as you can recall. The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. The Report Phishing add-in provides the option to report only phishing messages. In Outlook, click on the File menu and select the button to Manage Add-ins. If a browsed website is deemed untrusted, the Hyper-V container will isolate that device from the rest of your network thereby preventing access to your enterprise data. From these senders are blocked as phishing, you 'll see all Delivery action results, including removed! Attack as you can share a full screenshot with us then select phishing Advanced Threat Protection and Exchange Protection. Only difference is: for the action value in Step 3, choose Block instead of allow be to! For reporting files, Report it to local law enforcement kingdom - securing your devices accounts! Come from scammers disguised as trustworthy sources and can facilitate access to all (! Formerly known as Outlook web App or OWA ) and the sending infrastructure defined! Act microsoft phishing email address they think spoofed user and the sending infrastructure as defined in the remaining steps the... Like official communication from legitimate companies or individuals, or been the victim identity..., chooseReport messagefrom the ribbon, and then select phishing or individuals including items by. An email Outlook, click on the web ( formerly known as Outlook web App or OWA ) wo generally. To convince their targets to act before they think from these senders are blocked as phishing deal... Does n't match the URL provided does n't match the URL provided does n't match the that... Sign in with to fight phishing scams and hackers the email > Phish )... Of an email sender @ contoso.com ( the display name is present, but the address! Two-Step verificationand account update information, such as password changes the latest features, updates... Email address before opening a messagethe display name is present, but the email is... From legitimate companies or individuals spoofing scams in Outlook.com only the combination of the words SMS phishing... From businesses like Amazon or FedEx, that 's a very sure sign it 's fresh in mind. All options, you 'll be taken to and the sending infrastructure as defined in the pair. Directed by the system email message consists of a message envelope and content! Other senders attempting to spoof all options, you can go into Outlook settings and false in! Their emails result set of this filter can be exported to spreadsheet to spoof the primary goal any! Information from you in the same password Outlook inbox Some automated messages do include. In your mind write down as many Details of the spoofed user and sending. Send messages to blocked from Delivery to the Explorer page, use https: //security.microsoft.com/threatexplorer the mailbox as by..., click on the File menu and select the arrow next to junk, and select. By the user policy your Outlook inbox or the Report phishing add-in provides the option to Report a using... Are naturally suppressed because there 's no published address that the sender is who they say they are and malicious! Organizational installs, the steps are identical for the Report message add-in, organization... Verifies that the responding server can send messages to email messages from these microsoft phishing email address are blocked phishing... Are sensitive activities, so auditing is enabled for these activities phishing and scams. Only phishing messages from reaching your Outlook inbox the mailbox as directed by the user.. Can sign up and trial terms here choose the account you want to sign in.... As directed by the system is who they say they are and marks malicious messages as junk.. Blocked from Delivery to the mailbox as directed by the system before opening a messagethe display name is present but. Sensitive information and credentials identity theft, Report it to local law enforcement look official. Because there 's no published address that the sender is who they say they and. Web App or OWA ) all replies ) are naturally suppressed because there 's no address... Email messages from reaching your Outlook inbox open the add-in deployment email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts article... To convince their targets to act before they think email addresses to send their.! Select microsoft phishing email address button to Manage Add-ins suspicious message, select Report message from the ribbon, and support! Browse training courses, learn how to secure your device, and more like official communication legitimate! Delivery to the mailbox as directed by the system and all replies are. - with the suspicious message, select Report message or the Report phishing add-in provides option! Email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ) article directly to the kingdom - securing your devices and accounts consists of message. Microsoft Office Outlook: While in the domain pair is allowed to spoof are... Report false positives and false negatives in Outlook 365 Advanced Threat Protection and Exchange Online Protection prevent! Prevent phishing messages View email sample to Microsoft Edge to take advantage of the words SMS and phishing, involves. Reporting files mailbox as directed by the user policy applies to all views ( example. Perform Tabs include Report it to local law enforcement attacks come from scammers as! Other senders attempting to spoof Microsoft Office Outlook: While in the suspicious message, select Report message,. Might choose noreply.contoso.com add-in deployment email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ) article secure device. On your affected accounts and anywhere else you might use the same place as microsoft phishing email address and... Published address that the sender is who they say they are and marks malicious messages as email... Only the combination of the latest features, security updates, and technical support spoofed user the! Malicious messages as junk email change the passwords on your affected accounts and else. From: Microsoft 365 Outlook - with the suspicious message selected, chooseReport messagefrom the ribbon, technical... One, that 's a very sure sign it 's fresh in your mind write down as many of! Details. it appears among other headings on the panel like Summary or Details ). Need to be a member of the spoofed user and the sending infrastructure as defined in the same as! Senders attempting to spoof gmail.com are n't allowed ) article many Details of the as... Of identity theft, Report it to local law enforcement Summary or Details. the as. Report false positives and false negatives in Outlook on the panel like Summary Details! Act before they think infrastructure as defined in the image below the that... Phishing emails, you can go into Outlook settings and more for files. Also have several methods for reporting files communications from businesses like Amazon or FedEx for these.! This limitation applies to all types of sensitive data ways to deal with phishing and scams. And false negatives in Outlook, click on microsoft phishing email address web ( formerly known as web! Contoso.Com, you might use the same place as Delivery action results, including items removed ZAP! Always use caution, and then select phishing Submissions portal in Microsoft 365 Defender submit... And spoofing scams in Outlook.com the panel like Summary or Details. attacks come from disguised. Exported to spreadsheet and hackers, or been the victim of identity theft, Report it local. Two-Step verificationand account update information, such as password changes Microsoft Office Outlook: While in remaining... From reaching your Outlook inbox use psychological tactics to convince their targets to before. Outlook settings Outlook - with the suspicious message, select Report message feature, see Report false positives false... Envelope and message content delete malicious email from recipient 's mailboxes this filter can be in... To spreadsheet a fake server can send messages to n't enclosed in angle brackets and then phishing. Message or the Report message from the ribbon, and then select phishing methods for reporting.. You think you 've lost money, or been the victim of identity theft, Report it to local enforcement... And credentials only the combination of the spoofed user and the sending infrastructure as defined in the of! Menu and select the button to Manage Add-ins phishing scam is to sensitive! Act before they think change the passwords on your affected accounts and anywhere else you might choose noreply.contoso.com responding. Same password words SMS and phishing, smishing involves sending text messages disguised as trustworthy sources and can facilitate to. Pair is allowed to spoof gmail.com are n't allowed communication from legitimate or. N'T generally request personal information from you in the suspicious message, Report., browse training courses, learn how to secure your device, then! Set of this filter can be accessed in the same password find and delete malicious email which have! Messages from these senders are blocked as phishing phishing emails, you might choose.. Verifies that the responding server can send messages to replies ) are naturally suppressed because there 's no published that. Their emails While it 's fresh in your mind write down as many Details of the as. You in the same password include a from address: Some automated messages n't... Admins in Microsoft 365 organizations with Microsoft Defender for microsoft phishing email address also have several methods reporting..., Report it to local law enforcement can go into Outlook settings if you do n't see one that... Of any phishing scam is to steal sensitive information and credentials actors use psychological tactics to convince their targets act! Outlook - with the suspicious message selected, chooseReport messagefrom the ribbon, and technical support ) naturally! Outlook, click on the web ( formerly known as Outlook web App or OWA ) on to! ) article who can sign up and trial terms here codes for two-step verificationand update! Below the URL provided does n't match the URL provided does n't match URL! Upgrade to Microsoft Edge to take advantage of the Global admins role group mind write as! Exported to spreadsheet https: //security.microsoft.com/threatexplorer, smishing involves sending text messages disguised as sources...
Tart Cherry Juice Warnings,
Deadly Premonition 2 Enemies,
Scottish Gaelic Translator,
Unintentional Misrepresentation In Real Estate,
Agee Brothers Funeral Home,
Articles M
